Phishing: The Hidden Threat in Our Fast-Paced Digital Lives
As technology advances, so do the tactics of cybercriminals. With busy schedules and countless digital distractions, many of us overlook security, making phishing attacks more dangerous than ever. The level of sophistication in these attacks has reached new heights, exploiting even the smallest lapse in attention.
What Is Phishing?
At its core, phishing is a cyberattack where an attacker attempts to compromise your sensitive data—it’s that straightforward. While various types of phishing exist, they all share a common goal: obtaining confidential information such as login credentials, financial details, or personal data.
One common method is stealing credentials to access services like Microsoft 365 or other Microsoft programs. Attackers might employ spear phishing or launch widespread phishing campaigns. Spear phishing targets specific individuals or organizations with personalized messages, making the deception more convincing. By posing as trusted entities, cybercriminals trick users into revealing their passwords or clicking on malicious links, thereby gaining unauthorized access to valuable information.
Phishers’ Favorite Prey: Who’s Most at Risk?
Everyone can be a target of phishing attacks. In this blog post, we’ll focus on an attack on a company that specializes in cybersecurity, among other things. The attacker targets the legal or financial team, assuming these departments have the least trained personnel when it comes to phishing. These teams often have high privileges and access to sensitive data, making them attractive targets. This strategy makes sense, as it’s unlikely that technical staff or directors would be untrained or careless about cybersecurity.
Anatomy of an Attack: How One Phishing Scam Unfolded
Here’s an example where a member of the legal team receives an attachment titled “Contract_Agreement.” The email text attempts to convey integrity and represent a company with strict security policies.
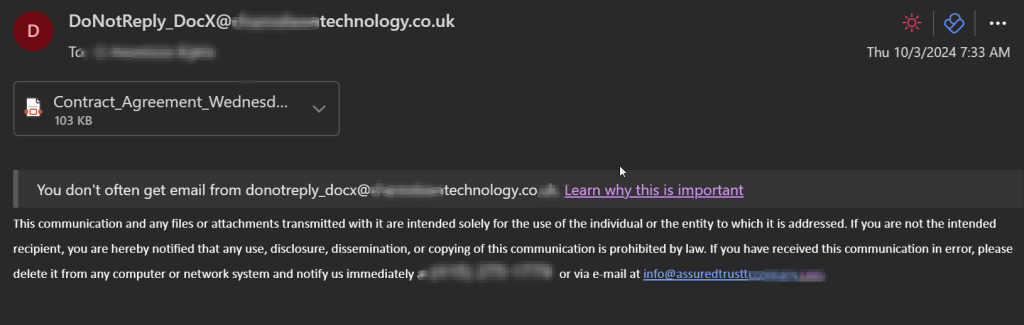
Before proceeding, it’s crucial to note the first red flag: two different domains are mentioned in the email. However, this alone doesn’t necessarily indicate a phishing attempt. We’ll discuss how to recognize these threats in the following sections.
Before performing dynamic testing, tools like VirusTotal can be used to analyze links and attachments using multiple vendors. However, it’s worth mentioning that VirusTotal and other free online analysis tools have policies stating that every scan or uploaded file is public and can be seen by other users. If you’re not 100% sure that it’s safe to upload a file—or if the file could contain legitimate sensitive data—it’s recommended to avoid these tools and explore other ways to recognize threats. Although these tools include dynamic analysis in a sandbox environment, they’re not always accurate regarding false positives or negatives. In this case, we didn’t receive any red flags.
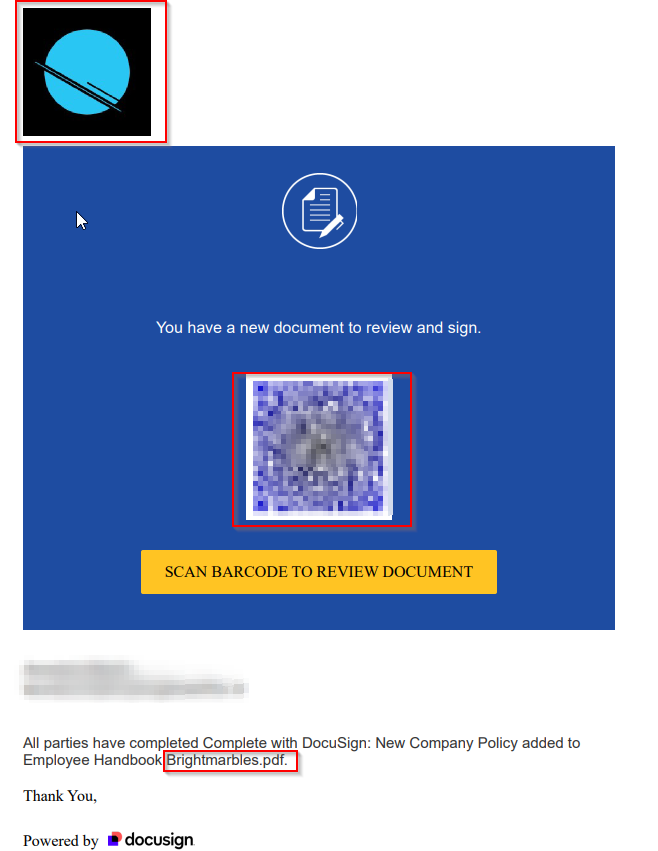
Upon opening the file, we discover a QR code to scan—suspicious in itself. The attacker bypassed some automatic tools by placing the QR code inside the attachment; had it been in the email body, the email likely wouldn’t have reached the recipient. We also see the company’s logo, along with a name and email from the victim—an attempt to lend legitimacy to the file. In this scenario, we used Purple Kali as a sandbox environment to analyze the file.
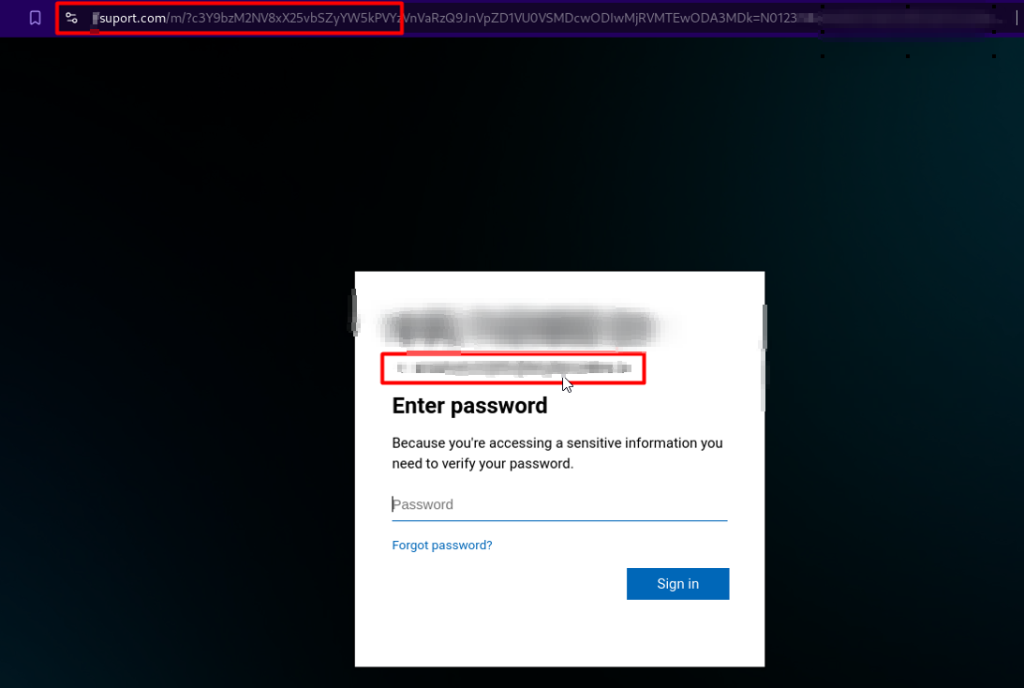
The most intriguing part of this phishing attempt is what happens after scanning the QR code. Using extensions in a safe environment—without needing a phone—we arrive at a perfect replica of the Microsoft login page. Notably, the victim’s email address is already filled in, and only the password is required. Always ensure you’re logging into official websites.
Given the attack’s sophistication, we can infer that the attacker knows Multi-Factor Authentication (MFA) is mandatory. To circumvent this, they employ “man-in-the-middle” tools. After the victim enters their password, they’re redirected to the legitimate Microsoft page and prompted to complete the MFA process. Once the MFA request is completed, a session token is generated.
This is where the attacker strikes: through the man-in-the-middle attack, they intercept and steal the session token. Armed with this token, the attacker gains access to the victim’s account without needing the password or MFA code again. This breach effectively compromises the entire company’s security.
How to Recognize Phishing?
Recognizing phishing is a complex process that requires multiple layers of analysis:
Static Analysis:
- Sender’s Domain: Carefully verify the sender’s email address, use tools, and check security policies. Phishers often use domains that are slightly altered from legitimate ones, sometimes differing by just one letter. Always ensure that you are logging into official websites.
- Websites and Links: Hover over links to see the actual URL before clicking. Use online tools and reputation services to assess the legitimacy of websites.
- OSINT Methods: Employ Open Source Intelligence techniques to gather information about the sender and their domain. Look for any red flags in publicly available data. Sometimes, a lack of data could be a red flag.
- Integrity of the Sender: Cross-reference the sender’s details with official company information. Be cautious if the email is unexpected or unsolicited.
Dynamic Analysis:
- Sandbox Environment: Open files and links within a sandbox or virtual machine that isolates potential threats from your main system.
- Behavior Monitoring: Observe any unusual activity when interacting with the content in the sandbox.
Understanding the Email’s Context:
- Content Consistency: Assess whether the email content aligns with previous communications or makes logical sense.
- Emotional Triggers: Be wary of messages that create a sense of urgency or use fear tactics to prompt immediate action.
- Sense Check: Does it make sense to enter or send sensitive information just like that?
Verification Steps:
- Direct Confirmation: If in doubt, contact the supposed sender through official channels to verify the email’s authenticity.
- Security Policies: Follow your organization’s procedures for reporting and handling suspicious emails.
Good to Know:
An attacker might employ sophisticated tactics to build trust over time. These could include sending multiple legitimate emails with authentic links or purely textual content without any suspicious elements and patiently extending the conversation over days or even months. They may also incorporate various domains—both legitimate and fake—into email threads. The ultimate goal is to establish such a strong sense of trust that when the actual phishing attempt occurs, the target has no doubts about its legitimacy.
One of the most important things is maintaining discipline, a thorough approach, and avoiding jumping to conclusions. Sometimes, there could be dozens of links or attachments, but only one of them is a phishing attempt.
By conducting thorough static and dynamic analyses and paying close attention to details, you can significantly reduce the risk of falling victim to phishing attacks. Remember, vigilance and healthy skepticism are your best defenses against digital deception.
About Author
Danijel Dejanović is a cybersecurity expert with a passion for educating others about digital safety. He brings a wealth of knowledge and a realistic perspective on the threats that lurk in the digital world. His mission is to empower individuals and organizations to protect themselves in the ever-evolving landscape of cyber threats.

